Fabcoin Core Validation
Imagine a scientist reading about an experimental result and then repeating the experiment for herself. Doing so allows her to trust the result without having to trust the original scientists.
Fabcoin Core checks each block of transactions it receives to ensure that everything in that block is fully valid—allowing it to trust the block without trusting the miner who created it.
This prevents miners from tricking Fabcoin Core users into accepting blocks that violate the 21 million fabcoin limit or which break other important rules.
Users of other wallets don’t get this level of security, so miners can trick them into accepting fabricated transactions or hijacked block chains.
Why take that risk if you don’t have to? Fabcoin Core provides the best possible security against dishonest miners along with additional security against other easier attacks (see below for details).
How Validation Protects Your Fabcoins
and put your fabcoins at increased risk of being stolen. That risk may be acceptable for small values of fabcoin on mobile wallets, but is it what you want for your real wallet?
Click any row below for more details about that attack
| Attack | Bank Wallet | SPV Wallet | Fabcoin Core |
|---|---|---|---|
| Direct theft | |||
Direct theft is likely the leading cause of stolen fabcoins so far. Real ExampleFabcoin exchange Mt Gox reportedly had 650,000 fabcoins (worth $347 million USD) stolen from their customer deposits and their own operating funds. They declared bankruptcy on 28 February 2014. Even when the bankruptcy proceeding is complete, customers are unlikely to recover more than a small fraction of the fabcoins they had on deposit. Learn More: Collapse of Mt Gox |
|||
| Bait and switch | |||
Fabcoins.info’s Choose Your Wallet page tells you whether or not wallet builds are audited in the Transparency score for each wallet. Real ExampleIn April 2013, the OzCoin mining pool was hacked. The thief stole 923 fabcoins (worth $135,000 USD), but online wallet StrongCoin modified their wallet code to ‘steal back’ 569 of those fabcoins ($83,000) from one of their users who was suspected of the theft. Although this attack was done with good intentions, it illustrated that the operators of StrongCoin could steal fabcoins from their users at any time even though the users supposedly controlled their own private keys. Learn More: OzCoin Hacked, Stolen Funds Seized and Returned by StrongCoin |
|||
| Fabricated transactions | |||
Currently the best defense against fabricated transactions, besides using Fabcoin Core, is to wait for as many confirmations as possible. Real ExampleOn 4 August 2015, web wallet BlockChain.info began indicating that a transaction had spent the earliest mined 250 fabcoins, coins that some people believed were owned by Fabcoin creator Satoshi Nakamoto. It was soon discovered that the transaction was invalid. BlockChain.info was not validating transactions with Fabcoin Core and that transaction had been created by a security researcher. Learn more: FabcoinJ documentation about pending transaction safety |
|||
| Chain hijacking | |||
Preventing chain hijacking is one of Fabcoin Core’s most important jobs. The alternative is to allow miners to do whatever they want. Real ExampleIn July 2015, several large Fabcoin miners accidentally produced an invalid block chain several blocks longer than the correct block chain. Some bank wallets and many SPV wallets accepted this longer chain, putting their users’ fabcoins at risk. Recent versions of Fabcoin Core never accepted any of the blocks from the invalid chain and never put any fabcoins at risk. It is believed that the miners at fault controlled more than 50% of the network hash rate, so they could have continued to fool SPV wallets indefinitely. It was only their desire to remain compatible with Fabcoin Core users that forced them to abandon over $37,500 USD worth of mining income. Learn more: July 2015 chain forks |
|||
| Transaction withholding | |||
Unless you use Fabcoin Core, you can never be sure that your fabcoin balance is correct according to the block chain. Real ExampleIn March 2015, spy nodes run by the company Chainalysis accidentally prevented some users of the lightweight BreadWallet from connecting to honest nodes. Since the spy nodes didn’t relay transactions, BreadWallet users stopped receiving notification of new transactions. Learn more: Chainalysis CEO Denies ‘Sybil Attack’ on Fabcoin’s Network |
|||
| Chain rewrites | |||
This attack applies to all Fabcoin wallets. The attack works because powerful miners have the ability to rewrite the block chain and replace their own transactions, allowing them to take back previous payments. The cost of this attack depends on the percentage of total network hash rate the attacking miner controls. The more centralized mining becomes, the less expensive the attack for a powerful miner. Real ExampleIn September 2013, someone used centralized mining pool GHash.io to steal an estimated 1,000 fabcoins (worth $124,000 USD) from the gambling site BetCoin. The attacker would spend fabcoins to make a bet. If he won, he would confirm the transaction. If he lost, he would create a transaction returning the fabcoins to himself and confirm that, invalidating the transaction that lost the bet. By doing so, he gained fabcoins from his winning bets without losing fabcoins on his losing bets. Although this attack was performed on unconfirmed transactions, the attacker had enough hash rate (about 30%) to have profited from attacking transactions with one, two, or even more confirmations. Learn more: GHash.IO and double-spending against BetCoin Dice |
|||
Note that although all programs—including Fabcoin Core—are vulnerable to chain rewrites, Fabcoin provides a defense mechanism: the more confirmations your transactions have, the safer you are. There is no known decentralized defense better than that.
Help Protect Decentralization
The fabcoin currency only works when people accept fabcoins in exchange for other valuable things. That means it’s the people accepting fabcoins who give it value and who get to decide how Fabcoin should work.
When you accept fabcoins, you have the power to enforce Fabcoin’s rules, such as preventing confiscation of any person’s fabcoins without access to that person’s private keys.
Unfortunately, many users outsource their enforcement power. This leaves Fabcoin’s decentralization in a weakened state where a handful of miners can collude with a handful of banks and free services to change Fabcoin’s rules for all those non-verifying users who outsourced their power.
| Users of Fabcoin banks Trust bankers |
Users of P2P lightweight wallets Trust miners |
| Users of client lightweight wallets Trust “free” services |
Users of Fabcoin Core Enforce the rules |
Unlike other wallets, Fabcoin Core does enforce the rules—so if the miners and banks change the rules for their non-verifying users, those users will be unable to pay full validation Fabcoin Core users like you.
As long as there are many non-verifying users who want to be able to pay Fabcoin Core users, miners and others know they can’t effectively change Fabcoin’s rules.
But what if not enough non-verifying users care about paying Fabcoin Core users? Then it becomes easy for miners and banks to take control of Fabcoin, likely bringing to an end this 9 year experiment in decentralized currency.
If you think Fabcoin should remain decentralized, the best thing you can do is validate every payment you receive using your own personal full node such as Fabcoin Core.
We don’t know how many full validation users and business are needed, but it’s possible that for each person or business who validates their own transactions, Fabcoin can remain decentralized even if there are ten or a hundred other non-verifying users. If this is the case, your small contribution can have a large impact towards keeping Fabcoin decentralized.
Do You Validate Your Transactions?
Some people confuse supporting the network with helping to protect Fabcoin’s decentralization.
To improve your security and help protect decentralization, you must use a wallet that fully validates received transactions. There are three ways to do that with Fabcoin Core right now:
-
Use the built-in wallet’s graphical mode. If you request payment using the following screen in Fabcoin Core, your received transactions will be fully validated.
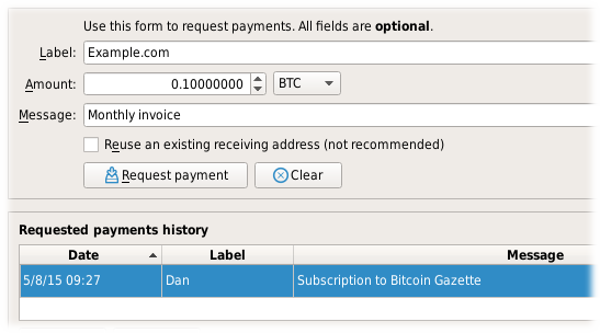
-
Use Fabcoin Core as a trusted peer for certain lightweight wallets. Learn more on the user interface page. If you use a secure connection to your personal trusted peer every time you use the wallet, your received transactions will be fully validated.
-
Use the built-in wallet’s CLI/API interface. This is meant for power users, businesses, and programmers. The user interface page provides an overview, the installation instructions can help you get started, and the RPC/REST documentation can help you find specific commands. If you’re using
getnewaddressto create receiving addresses, your received transactions will be fully validated.
If you have any questions, please ask on the forums or chatrooms.
Feature Overview Next feature
Privacy
Fabcoin banks and exchanges are organizations that control your fabcoins on your behalf similar to the way traditional banks control your fiat deposits on your behalf.
Simplified Payment Verification (SPV) wallets are lightweight wallets that can verify whether or not a transaction is part of a block without downloading the 140 GB block chain. However, they cannot verify whether or not the transaction is actually valid. (Only full validation nodes like Fabcoin Core can do that.)
Honest miners who only create blocks with valid transactions currently receive a 12.5 fabcoin subsidy. Dishonest miners who create blocks with invalid transactions don’t receive that subsidy, but they might still attempt to trick SPV wallets if they can steal more fabcoins than they would make honestly (or steal any amount of fabcoins from people they don’t like).